Microsoft Windows “God Mode” and other shortcuts
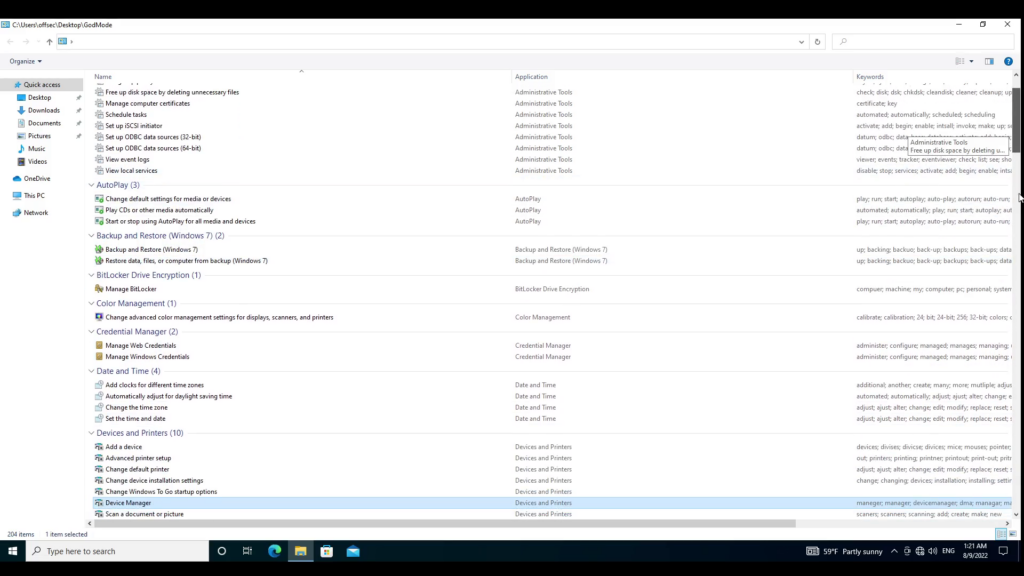
Recently, it came to our attention the existence of the so-called Windows “God Mode.” In reality, the “God Mode” is an alternative Control Panel with many options listed on one page. The most important feature of this “God Mode” Control Panel is that it makes it easier to find specific options and settings that Microsoft Windows developers hid for no apparent reason.
In the following video, we tried two methods to create the shortcut to the “God Mode” option, which was most likely named like this by people online rather than Microsoft.
Folder Method
The first method was to create a new folder and add the following string as the name of the folder:
GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
The result was the following: the folder’s icon changed, and the folder’s name disappeared.
When we double-clicked the new icon, it opened a window with the variety of options that we mentioned before.
Shortcut Method
The second method involved creating a shortcut. We used that method to preserve the folder’s name and select the icon we would keep.
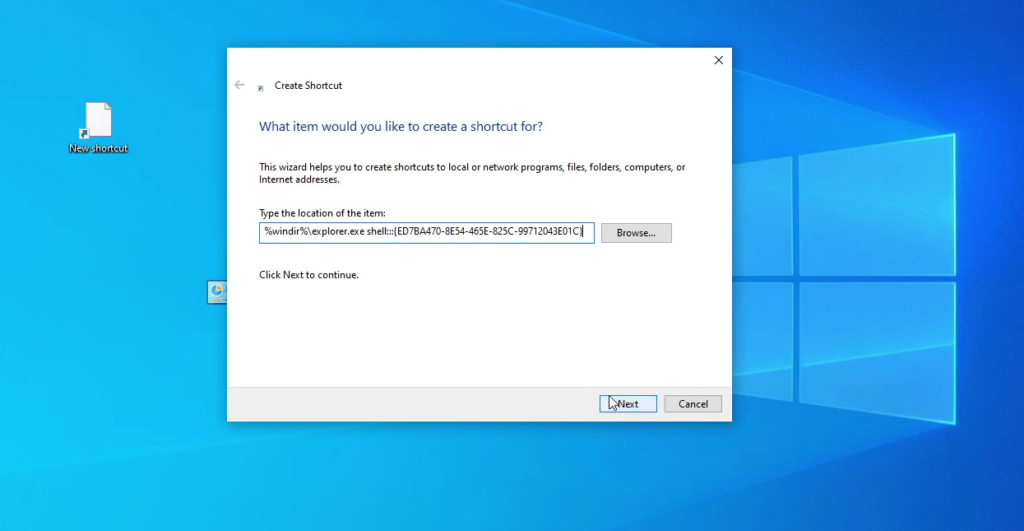
The first step was to create a new shortcut on the Desktop.
In the popup window, we set the following value at the “Type the location of the item:” option:
%windir%\explorer.exe shell:::{ED7BA470-8E54-465E-825C-99712043E01C}
Then we clicked on the “Next” button.
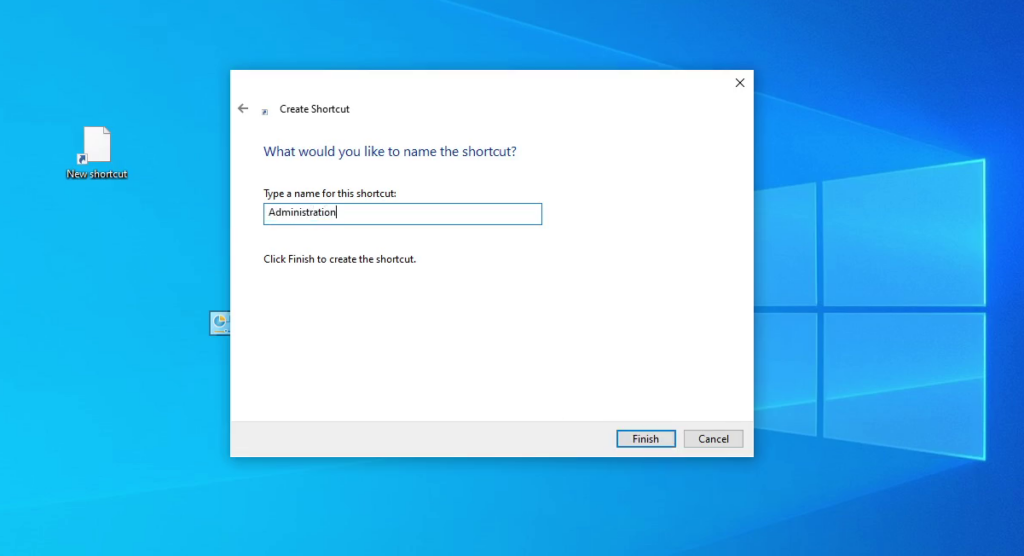
On the new page, we filled the “Type a name for this shortcut:” option with the value that we wanted to appear on the shortcut name. In our example, we used the word “Administration.”
After this, we clicked on the “Finish” button.
On the Desktop, our new shortcut appeared with the correct name. As we did not like the predefined icon, we right-clicked the shortcut and selected the “Properties” option. We clicked the “Change Icon…” button in the new window. Another window opened, we pressed the “Browse…” button and navigated to the file:
%windir%\System32\imageres.dll
After clicking the “Open” button, a new list of icons appeared from which we selected one that we liked, then clicked on the “OK” button. We clicked the “Apply” button on the remaining window, and Windows applied the icon change to our shortcut.
Additional “God Mode” codes
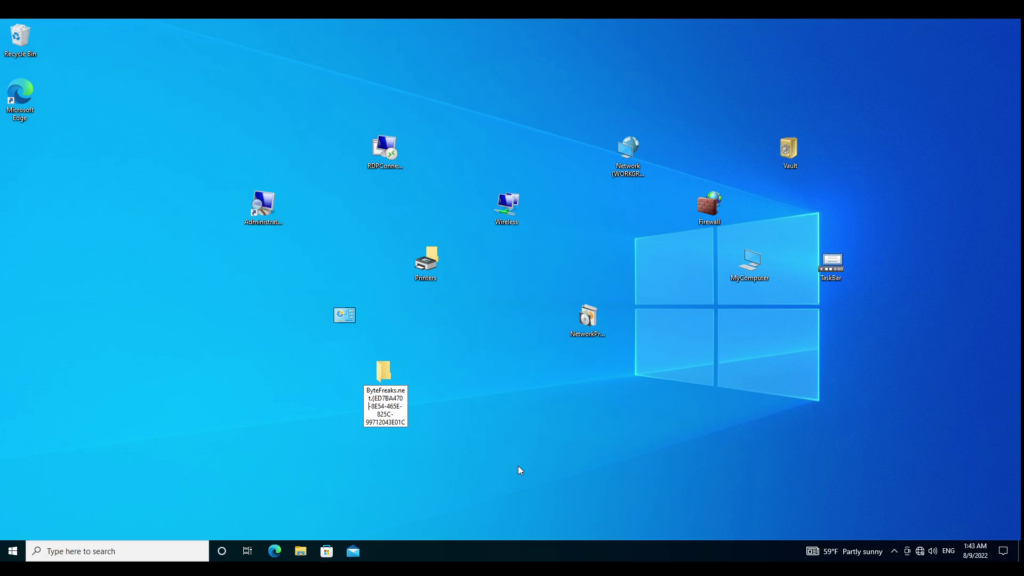
The following values allow you to create folders to specific items on your Windows PC.
Bytefreaks.net.{ED7BA470-8E54-465E-825C-99712043E01C}
TaskBarIcons.{05D7B0F4-2121-4EFF-BF6B-ED3F69B894D9}.
MyComputer.{20D04FE0-3AEA-1069-A2D8-08002B30309D}.
WinVault.{1206F5F1-0569-412C-8FEC-3204630DFB70}.
Firewall.{4026492F-2F69-46B8-B9BF-5654FC07E423}.
Network.{208D2C60-3AEA-1069-A2D7-08002B30309D}.
NetworkApplicationInstallation.{15EAE92E-F17A-4431-9F28-805E482DAFD4}.
Wireless.{1FA9085F-25A2-489B-85D4-86326EEDCD87}.
RDPConnecitions.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}.
Printers.{2227A280-3AEA-1069-A2DE-08002B30309D}.