Lubuntu LVM Encrypted
While trying to setup a lubuntu GNU/Linux that would use an encrypted LVM file-system we run into several problems that should have not been there.
For example, the installer would not continue as swap memory was not encrypted and it was blocking the operation.
An other issue was that the LVM support package was not installed by default although it is needed by the installer.
Our solution requires an active internet connection so that you can install the lvm2 package.
Methodology
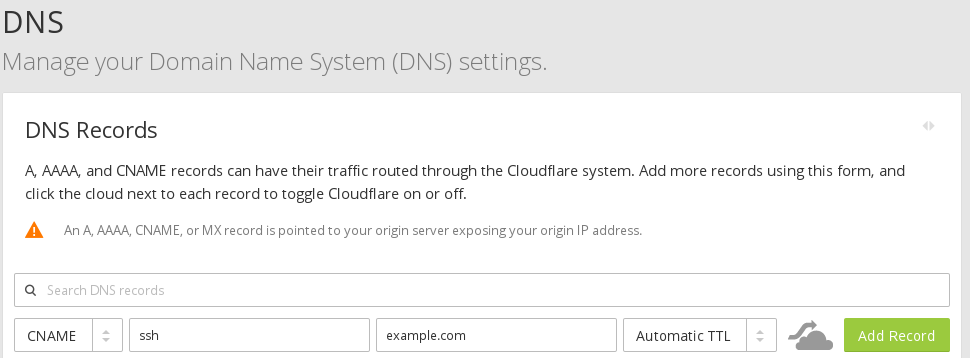
After booting into the live session, before we started the installation process, we opened a terminal from the main menu (Start Menu) and executed the following two commands:
sudo apt-get install lvm2 -y; sudo swapoff --all;
These two commands disabled all swap (so that we do not get the error that swap is not encrypted) and it installed the lvm2 package that is needed by the installer to create our LVM setup.
The following video presents the full successful installation procedure by making the changes before starting the procedure.
The next video, shows our attempts to fix the installation after encountering the errors instead of fixing them beforehand.