CloudFlare does not allow port 22 (usual SSH port) on domain 3
When you try to connect via ssh on a domain for which you are using CloudFlare as a HTTP proxy, you will get the following error:
$ ssh [email protected] ssh_exchange_identification: Connection closed by remote host
You have a few options to resolve for this issue:
- Either connect directly to the
IPof the machine. - Or, setup a
CNAMErecord with noHTTP proxyfor theSSH(so that you do not need to remember theIP).
This solution does not offer any additional benefits than connecting directly to theIPof the server.
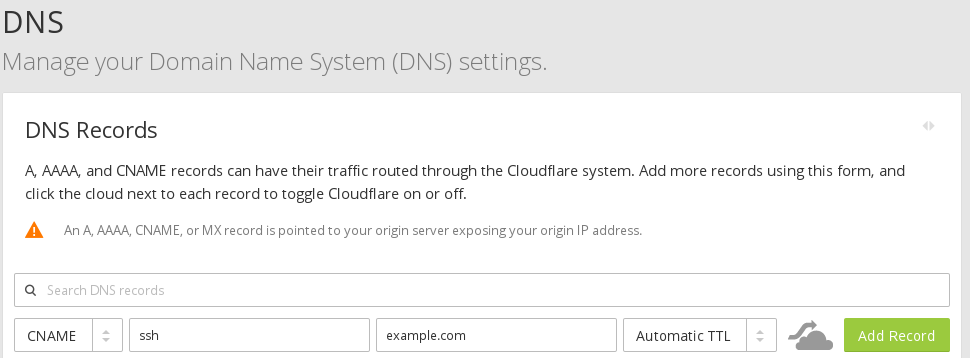
To do that, you need to visit the configureDNSpage for your site: e.g.https://www.cloudflare.com/a/dns/example.com,
then create theCNAMEnamedssh, use as target your domain (e.g.example.com) and disableHTTP proxyby clicking on the orange cloud and making it gray before pressing the
before pressing the Add Recordbutton.

Then, you will be able to connect viassh [email protected]. - Last solution but not least is configuring your server to listen for
SSHon one of the ports ofCloudFlarethat are open.
When this post was written, the following ports were available/open for any site inCloudFlare:
For requests made viaHTTP:80 8080 8880 2052 2082 2086 2095
For requests made via
HTTPS:443 2053 2083 2087 2096 8443
At the time, we were using an
Ubuntu GNU/Linuxserver, to instructUbuntu SSHDto listen to multiple ports we edited the file/etc/ssh/sshd_configand right after the lines:# What ports, IPs and protocols we listen for Port 22
we added another line with the new port we wanted to use:
# What ports, IPs and protocols we listen for Port 22 Port 2053
After restarting the service
service ssh restart;
we were able to connect to our page as follows:
ssh -p 2053 [email protected];