The Fugle Company – The optimal solution
Below you will find our take on the targeted attack game that was developed by Trend Micro.
With some luck and some good decisions, it seems that we got an optimal solution for this game that balances available resources while minimizing exposure risk. We will try and explain a bit our choices which happened to be the correct ones in this very interesting scenario.


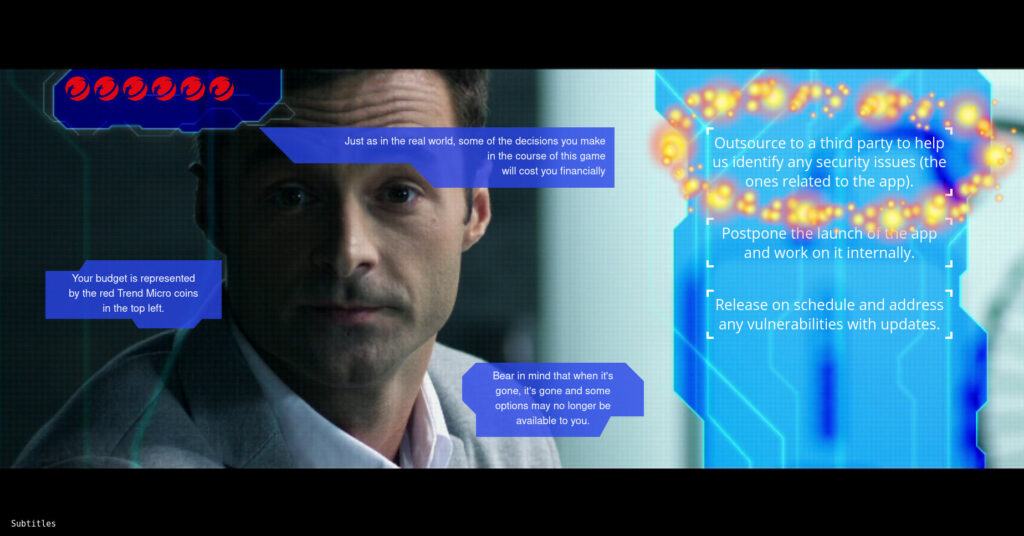
After being informed by our security manager that he is not sure if the product is ready when it comes to security, we chose the option “Outsource to a third party to help us identify any security issues (the ones related to the app).”. This way, we gave our security manager the chance to investigate further if there is a need to worry. 
When prompted with the three options for choosing the team to audit our system, we decided to pick “ITFr33X, recommended by one of the IT team members – a group of talented freelancers, who will do it fast and for a reasonable price.”.
We avoided using the clearly inexperienced team as their feedback might not be helpful in the end.
We also skipped the very experience team that was very expensive as we would spend 3 out of 6 tokens that are available to us on the initial investigation step. This way, we could starve the company of funds for development and improvement.
While trying to preserve some funds for new developments, we decided to use to the full extend our resources and picked the option “Use internal active directory to enforce strict access policies.”. It was clear that there was still a lot of space for improvement for free, so we thought it would be better to avoid making security changes while our base was not secured to its best settings. 
Assuming that no security infrastructure is perfect and that it is a matter of time before any product is hacked, we decided to take the option to “Encrypt all the Intellectual Property.” even though it had the cost of two tokens. This way, when our system might get compromised, we would at least protect all critical and sensitive data by rendering them useless to the attackers. 
We decided to improve our organization’s ability to detect and mitigate threats by selecting the option “Invest in Breach Detection technology.”. Again, we worked with the assumption that no security system is perfect, and it would be best to get our security systems up to date and improve our ability to detect, record, and prevent attacks and irregular behaviors. This option is a practical solution, and it provides immediate results to the system. 
We took the only option that seemed to make sense to us, which was “Invite them to the test the app in a controlled environment.”. Delaying the demo would give any journalist who wants to write a bad review for our company the stepping stone to do so. The option to provide access to the app with limited functionality had a lot of risks. It would allow an experienced user to mess with it and find problems exposing our company with severe consequences. 
Being straight with our responses regarding our intentions is a better option, in our opinion, than sugar-coating our answer while trying to trick the journalists. Since we were talking with an experienced journalist, the option “We are very sorry, but a high-security project, can not go outside the company.” would make sense to them, and we expected them to respect it. 
Since we were pretty confident with our systems, we believed that our team’s fast and thorough check was the best option. For this reason, we chose the option “Have the Security team check the Breach Detection System logs.”. 
SUCCESS!!
Below is a video demonstrating the gameplay we describe above.