Use Keytool to Create a New Keystore at your Windows Server
Step 1
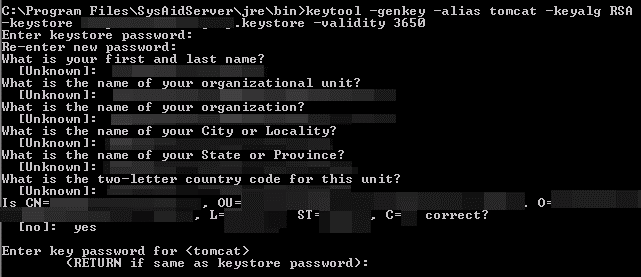
At your server, generate the Keystore file using keytool command at your command line window with the following command:
keytool -genkey -alias tomcat -keyalg RSA -keystore your_site_name.keystore -validity 3650
In the command above, your_site_name should be the name of the domain you want to secure with this SSL/TLS certificate.
When prompted for the first and last name, type the Fully Qualified Domain Name (FQDN) for the site you are securing with this certificate (e.g., www.yourdomain.com, mail.yourdomain.com).
Step 2
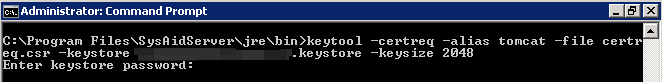
Generate a Certificate Signing Request (CSR) from your New Keystore using the keytool command:
keytool -certreq -alias tomcat -file certreq.csr -keystore your_site_name.keystore -keysize 2048
When prompted, enter the password you created earlier (when you created your new Keystore).
In your current directory, certreq.csr now contains your CSR.
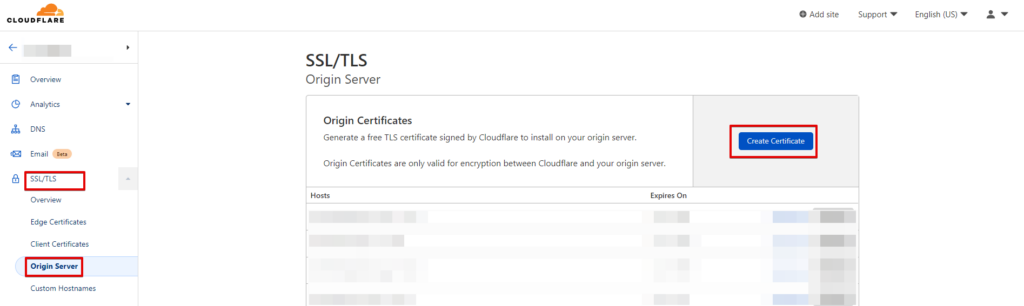
Create the certificate from Cloudflare using the certificate request that you created from your Windows Server
Step 3
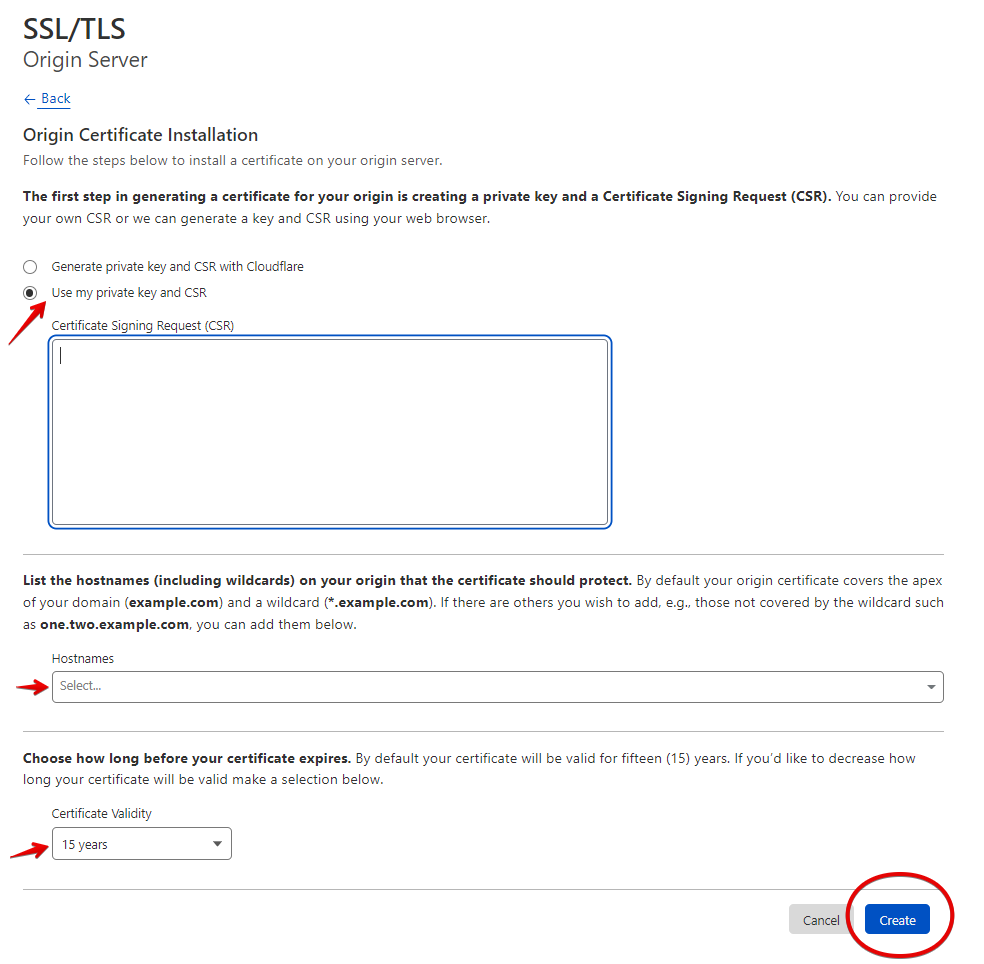
Open your Cloudflare account, select your domain, open the SSL/TLS tab and click on Origin Server to create the certificate
Step 4
Select the option I have my own private key and CSR where you will Copy-Paste the certificate you saved on the txt file from your Windows Server (certreq.csr), fill in the hostnames, select the expiration years, and press Create
Step 5
Copy-Paste in PKCS#7 key format the certificate in a text file and save the file
Import Cloudflare Origin CA root certificate at your Windows server
Step 6
Copy the Cloudflare Origin CA — RSA Root certificate from the Cloudflare website, save to a file and transfer it to your Windows Server.
[https://developers.cloudflare.com/ssl/origin-configuration/origin-ca/#4-required-for-some-add-cloudflare-origin-ca-root-certificates]
Filename: origin_ca_rsa_root.pem
Step 7
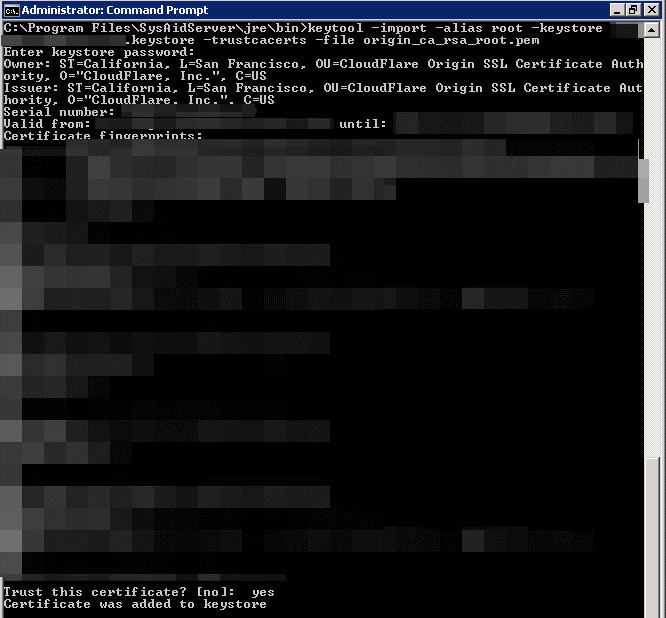
Import the root certificate into your Keystore file.
keytool -import -alias root -keystore your_site_name.keystore -trustcacerts -file origin_ca_rsa_root.pem
Add the public certificate from Cloudflare to your Windows Server
Step 8
Copy the file with the PKCS#7 certificate from Cloudflare at your Windows Server
Step 9
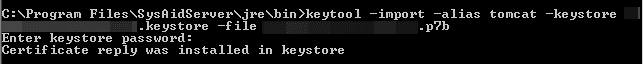
Run the following command to import the public certificate at your Keystore
keytool -import -alias tomcat -keystore your_site_name.keystore -file your_site_name.p7b
You should get a confirmation that the “Certificate reply was installed in Keystore.”
Use the newly created server origin certificate from Cloudflare for your website.
Step 10
Find your Tomcat server configuration (server.xml file), make the following changes at your Connector, and save the file.
<Connector executor="tomcatThreadPool" port="443" protocol="HTTP/1.1" SSLEnabled="true"
maxThreads="150" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS" keystoreFile="C:\Program Files\SysAidServer\ keystore your_site_name.keystore" keystorePass="XXXXXXXXXXXXXX" />
Step 11
Restart the Tomcat service