Hikvision web UI cannot change admin password
Note / Disclaimer / Caution / Warning: We are not sure if the same commands will work on your device! Following these instructions has some risk as not everything is well documented and could damage your device and make it unable to be repaired or used! We are posting about our experiences as it might help someone else but we cannot guarantee positive results to other people. We got lucky, we cannot be sure if this works for everyone...
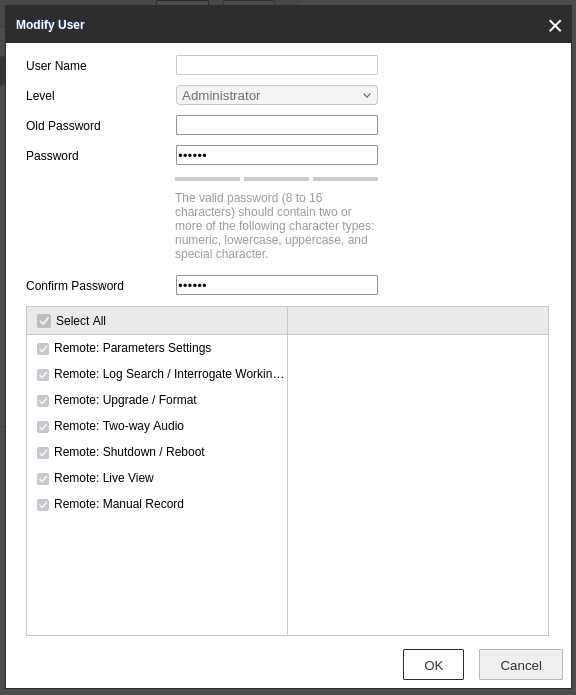
Recently, we were performing maintenance on a Hikvision DS-KB8112-IM Vandal-Resistant Door Station. When we tried to change the password for the default administrator (called admin) we noticed that we could not edit the user. There was a bug in the list of users which was not showing the username of the admin.
That bug caused the Modify functionality to fail as well. It would leave the User Name field as blank which would trigger an error after pressing the OK button. The system complained that the User Name field is empty while it is required making the change of password to fail.
We could not figure out a way to fix it through the menus of Hikvision nor could we flash or update the device firmware, so after some search, we found the documentation of some API (which we are not sure if is actively maintained) that allowed us to get the settings of the device and update them.
Specifically, using the following command, we got the list of users on the Hikvision device:
curl -k 'https://admin:[email protected]/ISAPI/Security/users';
The GET of ISAPI/Security/users gave us the list of all users like so:
<?xml version="1.0" encoding="UTF-8" ?>
<UserList version="2.0" xmlns="http://www.isapi.org/ver20/XMLSchema">
<User version="2.0" xmlns="http://www.isapi.org/ver20/XMLSchema">
<id>1</id>
<userName>admin</userName>
<bondIpAddressList>
<bondIpAddress>
<id>1</id>
<ipAddress>0.0.0.0</ipAddress>
</bondIpAddress>
</bondIpAddressList>
<bondMacAddressList>
<bondMacAddress>
<id>1</id>
<macAddress>00:00:00:00:00:00</macAddress>
</bondMacAddress>
</bondMacAddressList>
<userLevel>Administrator</userLevel>
<attribute>
<inherent>true</inherent>
</attribute>
</User>
</UserList>
Then, for fun, we issued the command that returns the information for the admin user (that has the ID = 1):
curl -k 'https://admin:[email protected]/ISAPI/Security/users/1';
<?xml version="1.0" encoding="UTF-8" ?>
<User version="2.0" xmlns="http://www.isapi.org/ver20/XMLSchema">
<id>1</id>
<userName>admin</userName>
<userLevel>Administrator</userLevel>
<attribute>
<inherent>true</inherent>
</attribute>
</User>
Then we went for the risky part, to issue a command that would edit the settings of the device with great risk!
curl -k 'https://admin:[email protected]/ISAPI/Security/users/1' -X PUT --data-raw $'<User version="2.0" xmlns="http://www.isapi.org/ver20/XMLSchema">\n<id>1</id><userName>admin</userName><password>4321</password></User>';
The PUT command for ISAPI/Security/users/1 loaded the following XML to the device:
<User version="2.0" xmlns="http://www.isapi.org/ver20/XMLSchema">
<id>1</id>
<userName>admin</userName>
<password>4321</password>
</User>
To our pleasant surprise, it worked! After executing the above command, we were able to log in to the device using the new password. To an even more pleasant surprise, the list of users bug disappeared and we were able to use the web GUI to make changes to the administrator user!